
Choosing the right IT asset disposition (ITAD) provider for your company is a decision that requires careful consideration. It's not just about disposing of old tech—it's about ensuring any information contained on that old tech is destroyed securely and responsibly. This is important because it is your company, not your ITAD provider, who is ultimately liable in the event of a security breach if those assets are not handled professionally, and your company or customer information ends up in the wrong hands. Here’s how to make the right choice and safeguard your company’s data.
Data Security is Your Responsibility
Ultimately, your company is liable for any information contained on your old IT assets, even during ITAD procedures being handled by professional providers. This is why it's crucial to select a provider who is upfront about their data destruction process. They should also maintain a meticulous chain of custody and offer audit trail assistance. Be cautious of any provider who leaves the responsibility of information security entirely to you without clearly outlining their procedures. This might be a red flag indicating their methods aren't up to par.
The True Cost of Data Breaches
A big worry with handling your own IT asset disposition or using a less-than-reputable provider is the potential for a data breach. If that happens, the financial hit could be way bigger than any savings you thought you'd get.
In the U.S., the average cost of a data breach was a whopping $9.44 million in 2022, and that number is only going up. Around the world, countries are creating laws to protect people's personal information. Even though there's no single data protection law in the U.S., there are tons of federal and state laws that protect personal information. For example, you've got the Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Technology for Economic and Clinical Health (HITECH) Act for healthcare information, the Sarbanes-Oxley Act for public companies, and the Gramm–Leach–Bliley Act for financial institutions, in addition to countless others. If your company experiences a data breach due to improper ITAD, these laws that protect your customers could cause serious financial and reputational damage to your company. That is why using a professional, dedicated ITAD provider is critical in mitigating that risk.
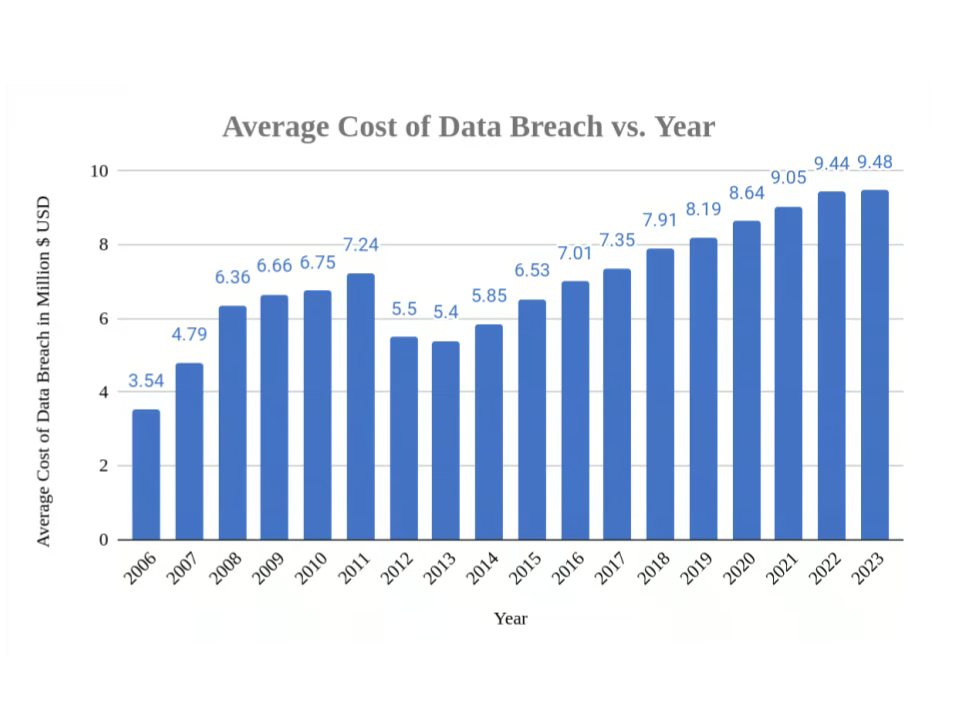
Image: The Cost of Data Breaches in the USA, Data from Statista.
What to Look for in an ITAD Provider
Adherence to Stringent NIST 800-88 Standards
Your chosen provider and their processors should have the skills and tools needed to perform secure data wiping according to stringent NIST 800-88 r1 data destruction standards. According to these standards, drives are securely wiped using approved methods. Then, each and every single drive must be verified for data erasure. Drives that fail the verification process must be physically destroyed. This process helps protect against data breaches while promoting a circular economy by securely wiping drives as the best option to encourage their reuse and only using physical destruction when necessary.
Companies that are not transparent about the standards that they use or try to pass the responsibility off to you or their third-party providers should be avoided. Those are red flags that they do not take your data security as seriously as they should. Failing to follow best practices can expose your company to significant risks, including fines, litigation costs, and damage to your brand reputation.
Data Destruction Certificates
Your provider should offer certificates of data destruction for your assets, trackable by serial number, so that you can track assets and ensure the information was destroyed. Ideally, they should have an online portal for you to access those certificates yourself so that you have them when you need them. However, this requirement is not critical. These certificates are critical to obtain and keep on record to show your due diligence during internal and external audits and ensure you are in compliance with data privacy laws.
A Meticulous Chain of Custody
Choose an ITAD provider who offers a meticulous chain of custody to ensure that assets are not misplaced, left in insecure locations, or handed off to an unqualified processor before data destruction has taken place, as these risks are where data breaches are the most likely to occur. And don’t simply take their word for it. Choose a provider who offers real-time tracking through an online portal so you can check where your assets are at all times throughout the ITAD lifecycle. This level of transparency gives you the assurance that they will never cut corners because all their activities are documented in real-time. This helps ensure a meticulous chain of custody from initial pickup to final disposition, whether through refurbishment and resale or recycling. They should offer a chain of custody documentation showing where each asset ended up in the final disposition.
ICT: Setting High Standards for Data Destruction
ICT is a managed ITAD service provider that uses a nationwide team of vetted logistics handlers specializing in the secure transportation of IT assets. They are a DLA-certified DOD contractor that uses stringent NIST 800.88 data destruction procedures, including the verification of erasure of every drive. Those drives are responsibly repurposed or physically destroyed according to client requirements. Drives that cannot be appropriately wiped are physically destroyed to ensure the ultimate client’s data security. Certificates of data destruction with a serialized list of all drives handled and reconciled by number and weight to ensure all assets are accounted for come with every project and can be accessed online on demand. Then, you can rest assured that your company and customer information are safe and secure.
Case Study: ICT provided a compliant ITAD solution for a manufacturing company in Ohio, which involved disposing of 155 assets and erasing 162 HDDs according to NIST 800.88 standard, protecting their data security and brand reputation. Our service costs were offset by the value of the equipment.
The Bottom Line
Choosing the right ITAD provider is about more than just disposing of old equipment. It's about ensuring your data is destroyed securely in compliance with the highest industry standards. By selecting a provider that offers comprehensive services, maintains transparency, and adheres to stringent data destruction methods, you can protect your company from potential risks and ensure a smooth and secure ITAD process.
Find Out How We Can Help
If you are an enterprise, government, or institution looking for ITAD solutions or want a copy of our white paper on Data Destruction comparing the services provided by 8 major ITAD providers, please** contact us at ICT**.
Selected References
Assistant Secretary for Planning and Evaluation (ASPE). (1996, August 20). Health Insurance Portability and Accountability Act of 1996. ASPE. https://aspe.hhs.gov/reports/health-insurance-portability-accountability-act-1996
Bloomberg. (2023, December 12). Consumer Data Privacy Laws. Bloomberg Law. https://pro.bloomberglaw.com/insights/privacy/consumer-data-privacy-laws/
Congress.gov. (2002, July 24). H.R.3763 - 107th Congress (2001-2002): Sarbanes-Oxley Act of 2002. Congress.gov. https://www.congress.gov/bill/107th-congress/house-bill/3763
DLA Support Services. (2024). Dla.mil. https://www.dla.mil/What-DLA-Offers/Support-Services/
ICT Mission Reuse (2022). Reuse Technology Through a Stress-Free Solution that Pays Cash. https://mission-reuse.com/
Kissel, R., Regenscheid, A., Scholl, M., & Stine, K. (2014, December 17). Guidelines for Media Sanitization. Csrc.nist.gov. https://csrc.nist.gov/pubs/sp/800/88/r1/final
Statista. (2024). Cost of a data breach in the U.S. 2024 | Statista. https://www.statista.com/statistics/273575/us-average-cost-incurred-by-a-data-breach/#:~:text=Published by Ani Petrosyan%2C Sep
©ICT Inc. 2024-2027. All rights reserved. Unauthorized reproduction, distribution, or use of this article, in whole or in part, without proper attribution to ICT Inc. is strictly prohibited.
